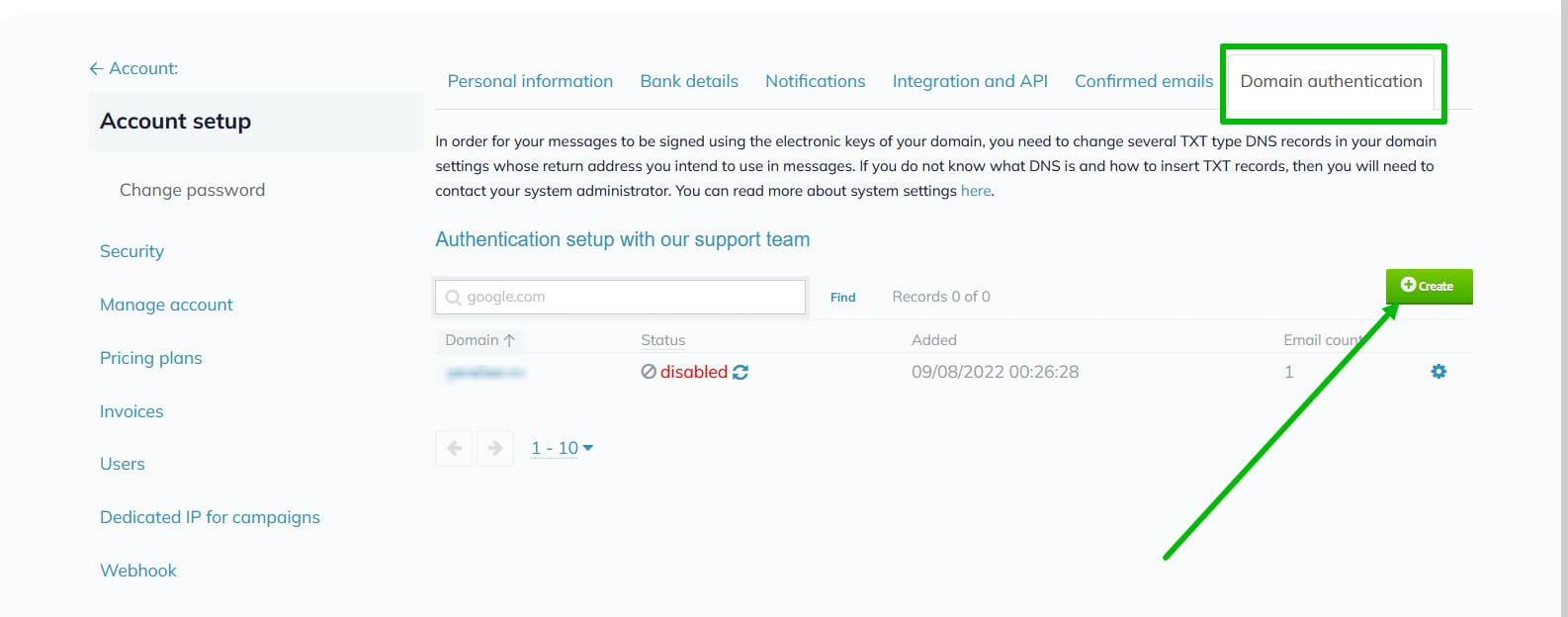
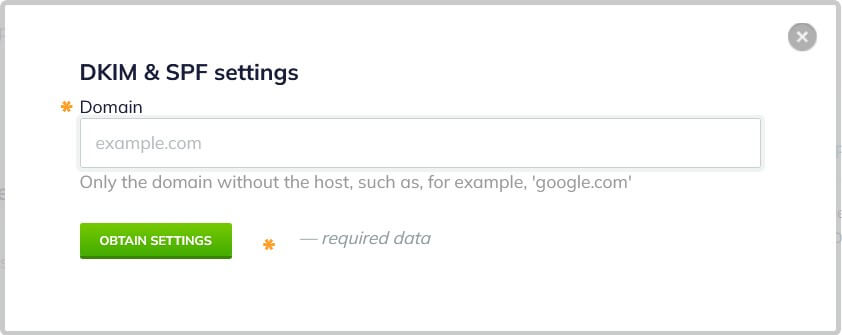
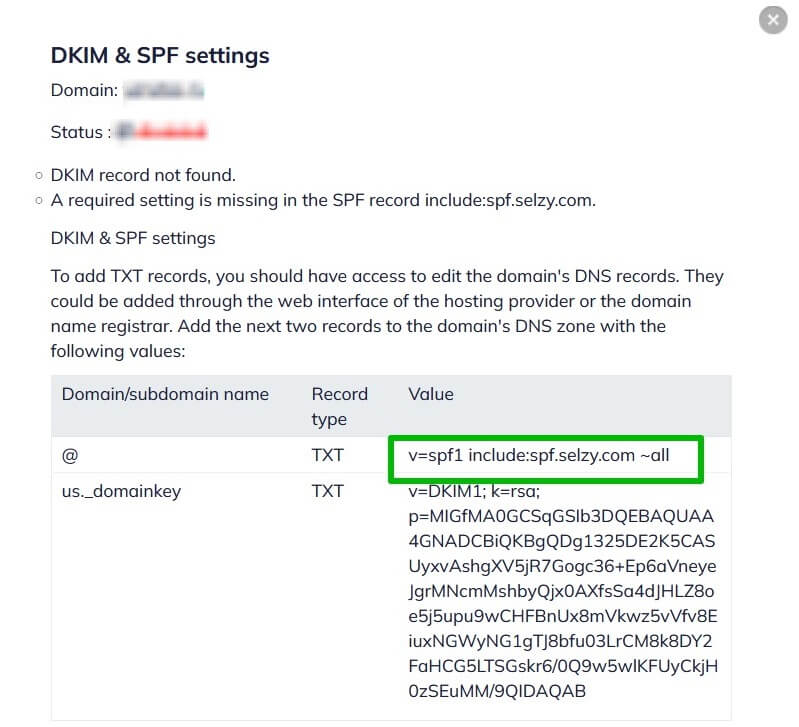
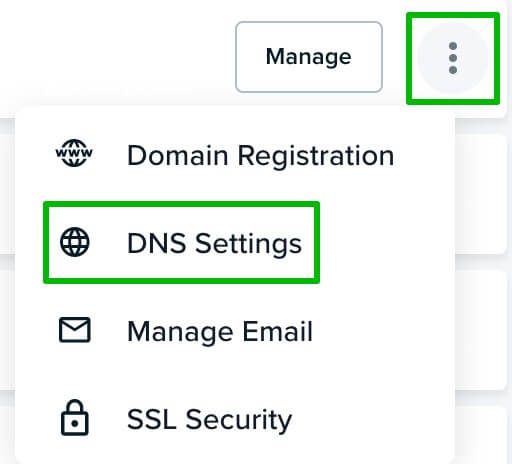
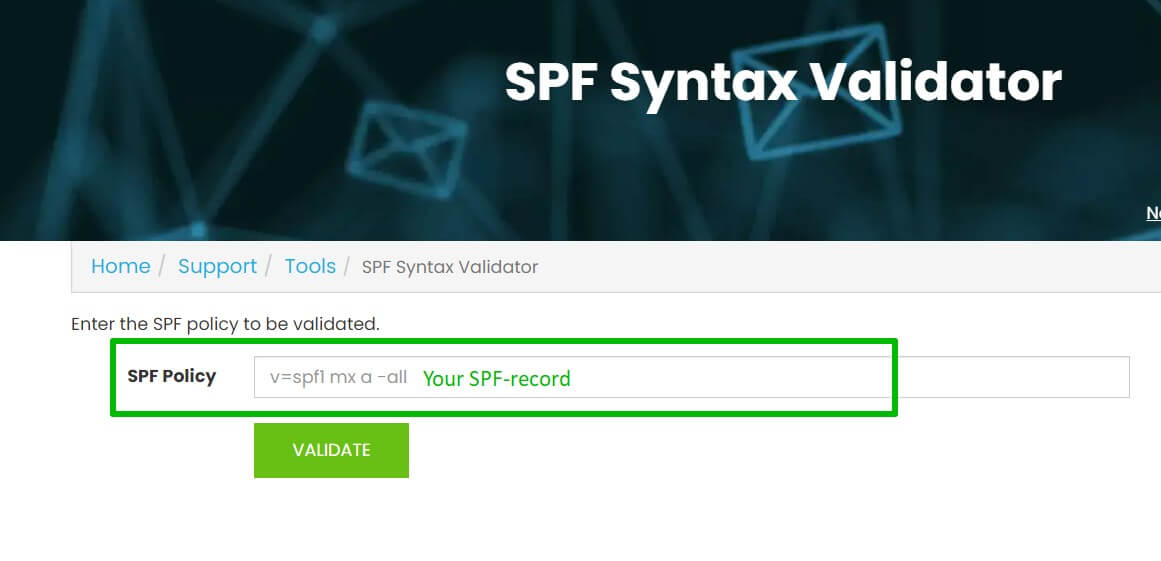
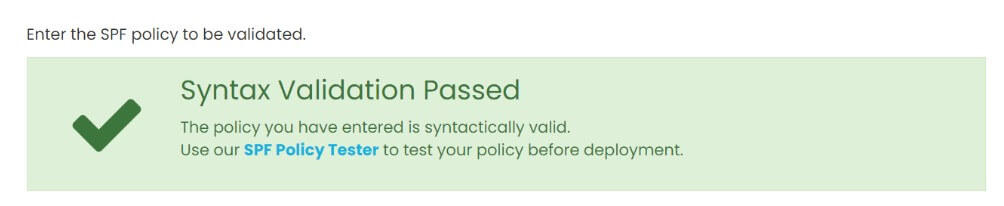
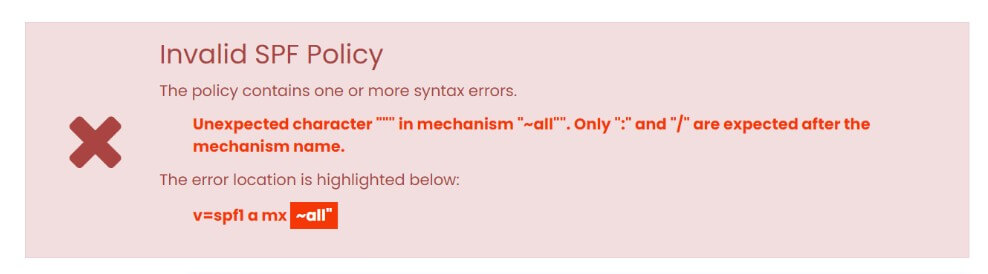
What is SPF
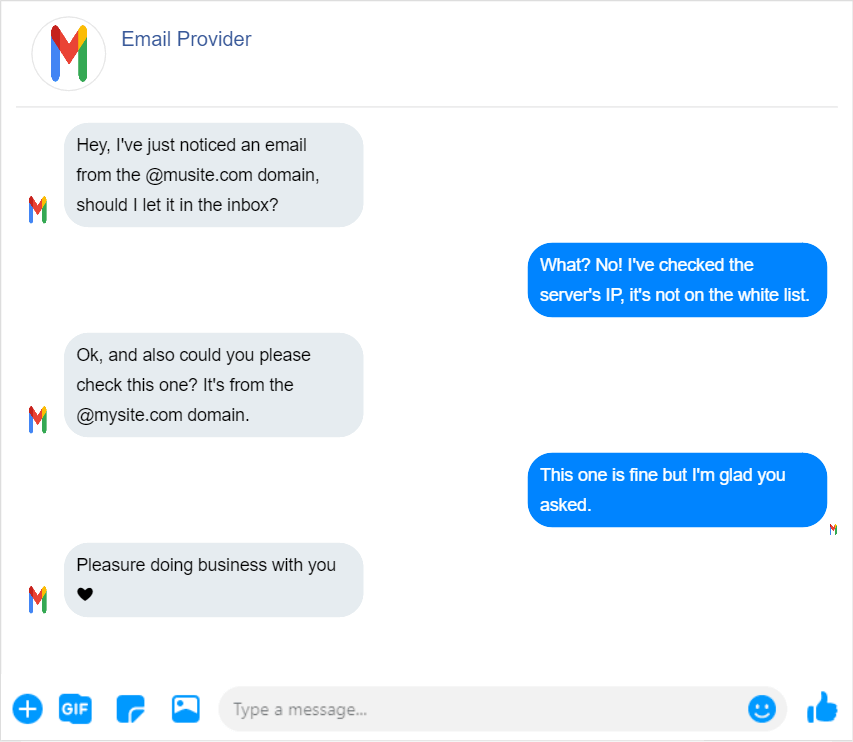
SPF, or Sender Policy Framework, is a method of email authentication that helps to prevent email spoofing. In email spoofing, someone pretends to be the sender of an email by forging the sender’s email address.
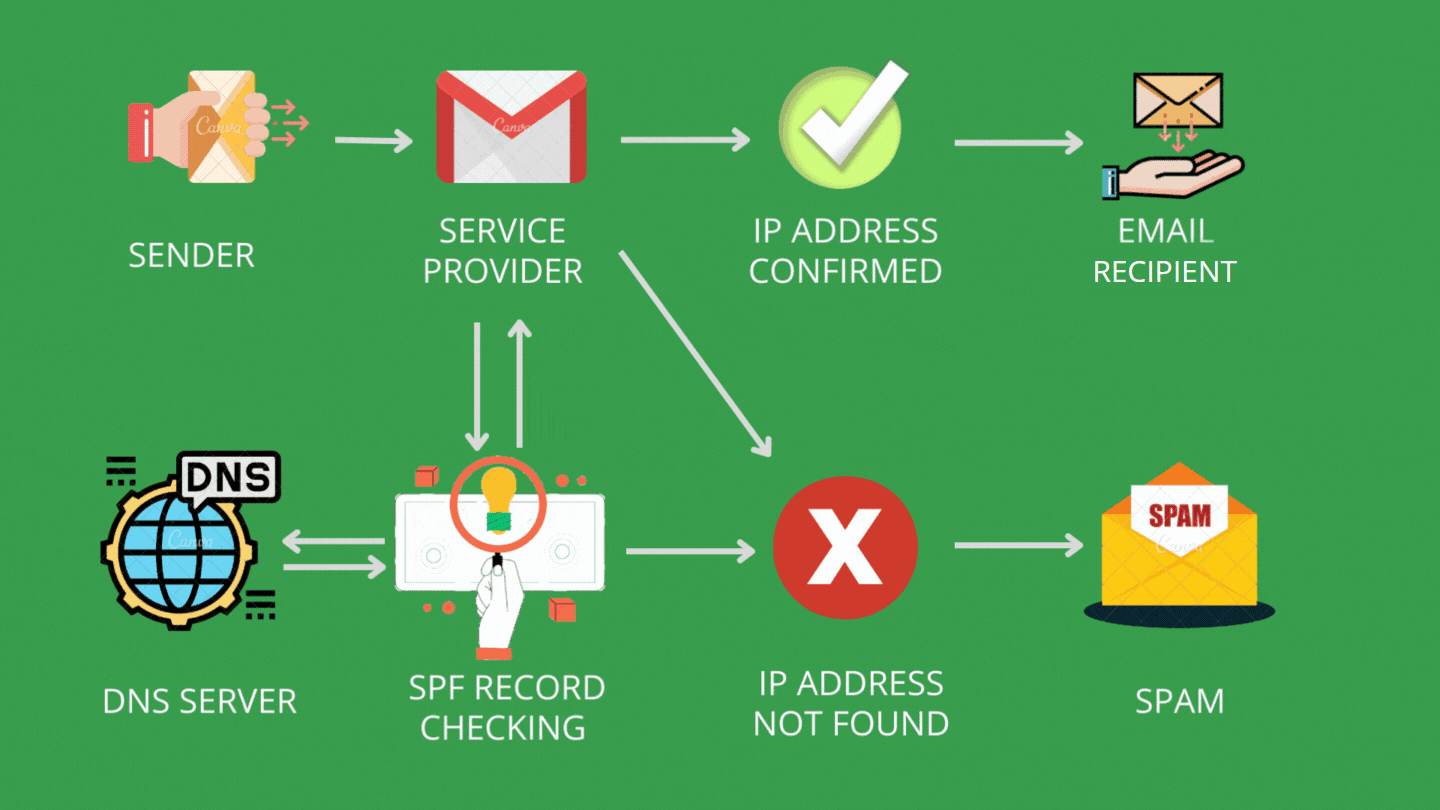
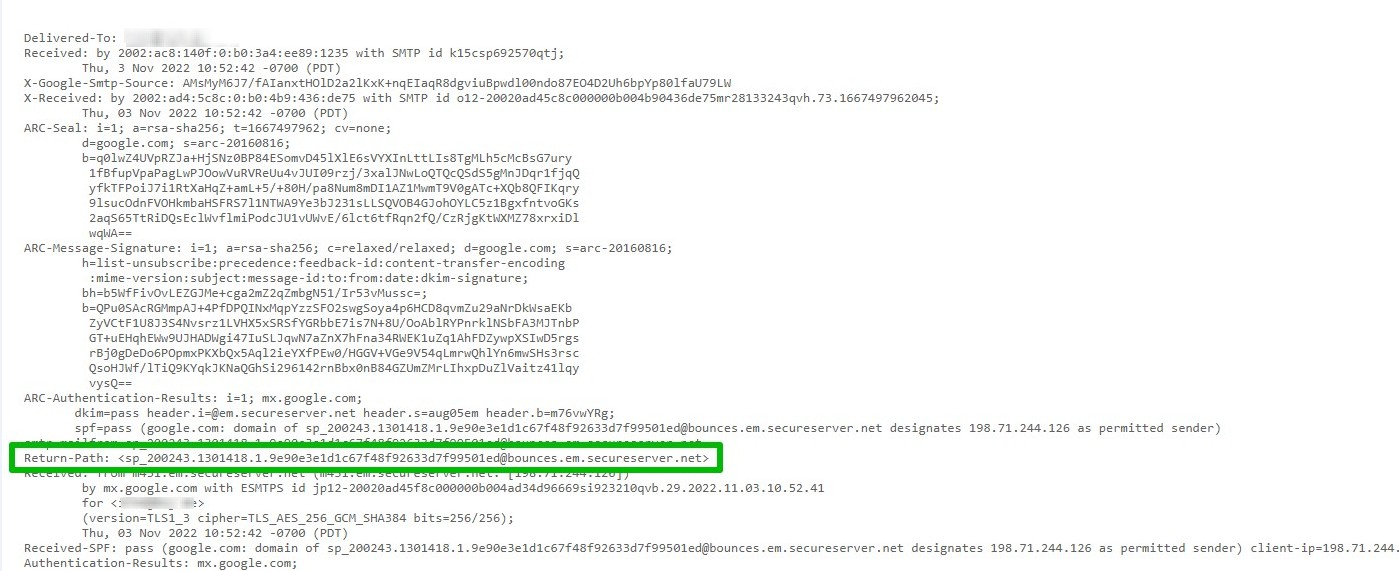
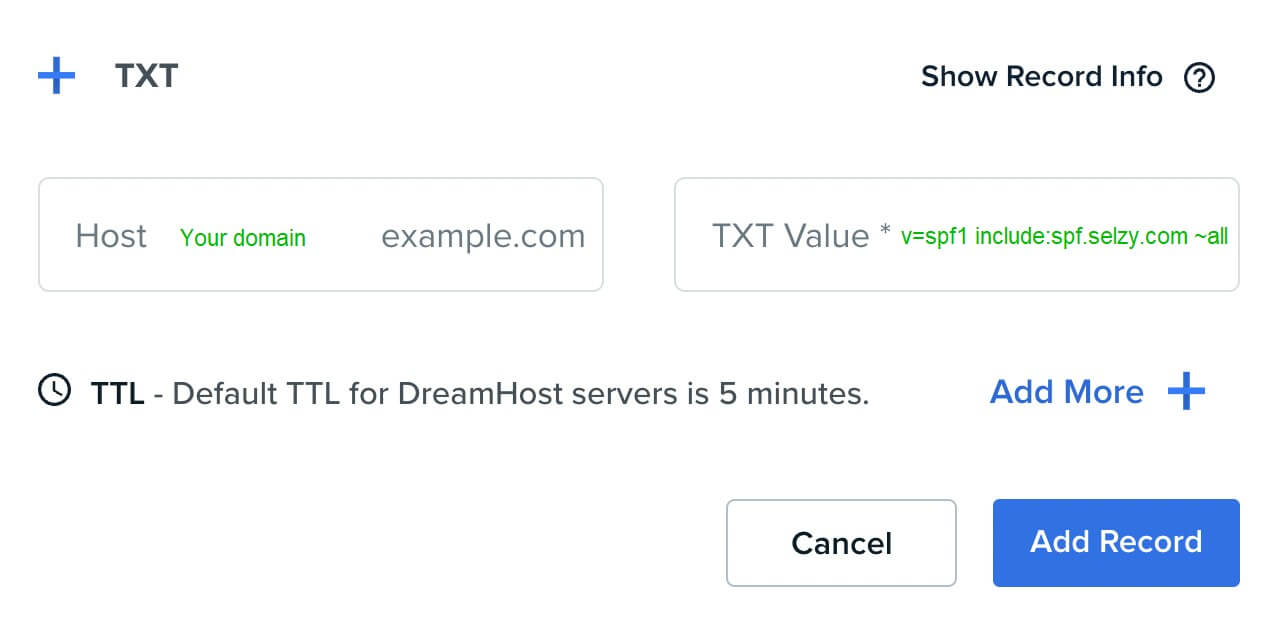
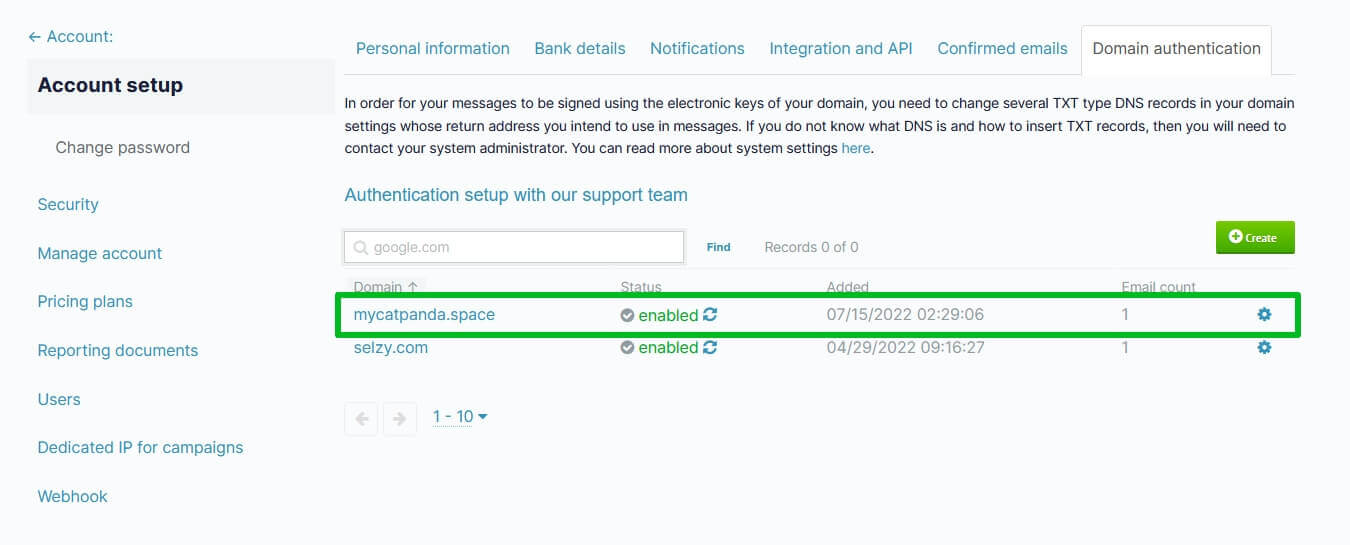
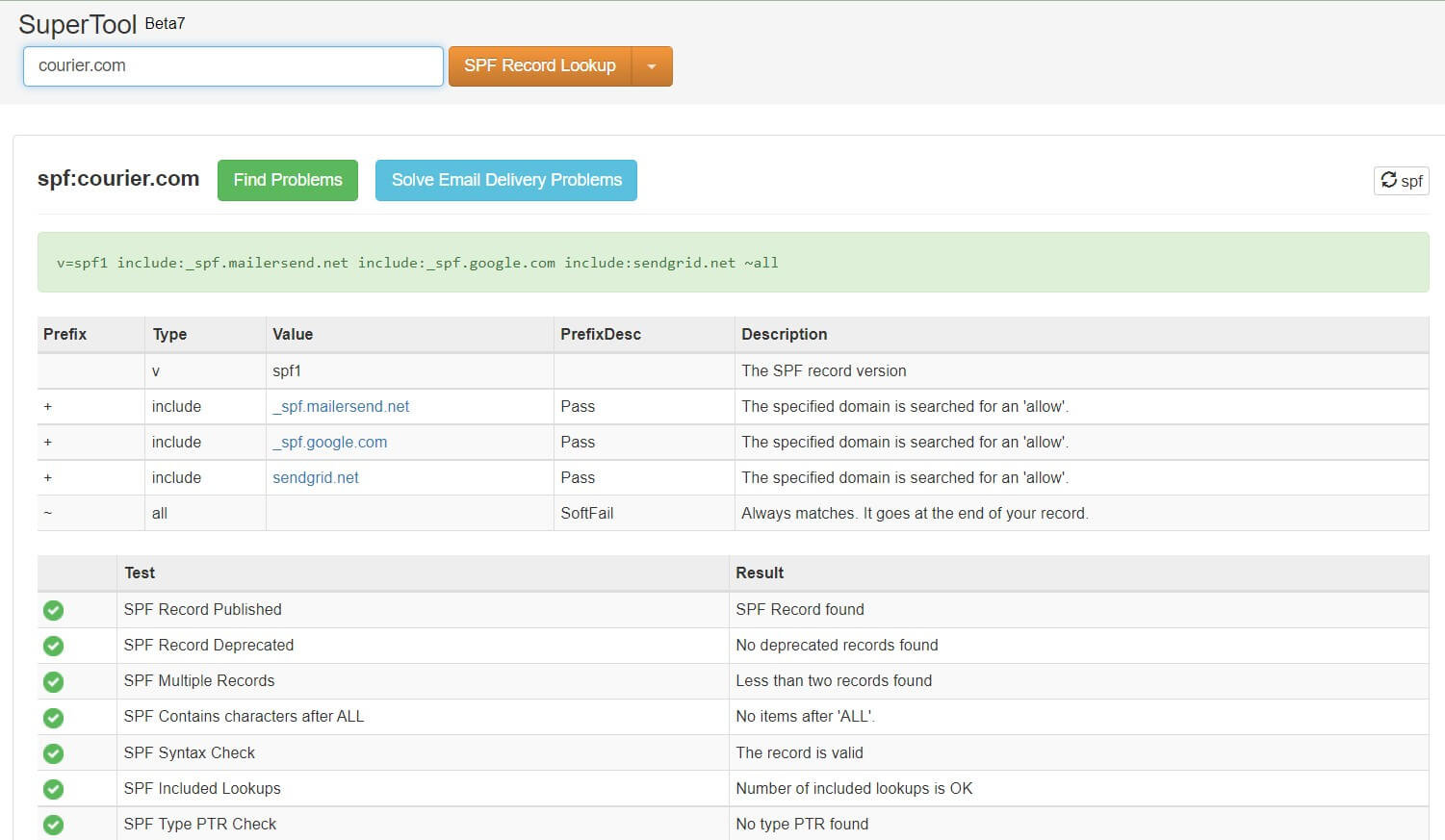
Using SPF, the true owner of an email domain can specify which servers and IP addresses are allowed to send emails from that domain. This information is published in the domain’s DNS records. When an email is received, the receiving server checks the SPF record to verify that the email is indeed coming from an authorized server for that domain. If not, it may mark the email as spam or reject it.
It is important to note that SPF only authenticates the sending server and does not necessarily verify the sender’s identity. For more thorough email authentication, it is recommended to combine SPF with DKIM, DMARC, and BIMI which can result in major improvements to your email security.