DMARC setup process step-by-step
We’ve discussed what DMARC is, how it works, and why your business needs it. Now let’s take a closer look at how to set up a DMARC record for your company’s emails.
Prepare to set up
Regardless of the email provider you use, DMARC won’t work without SPF and DKIM. That’s why during the preparation stage you need to set those up.
Setting up SPF. It takes four steps to set up SPF:
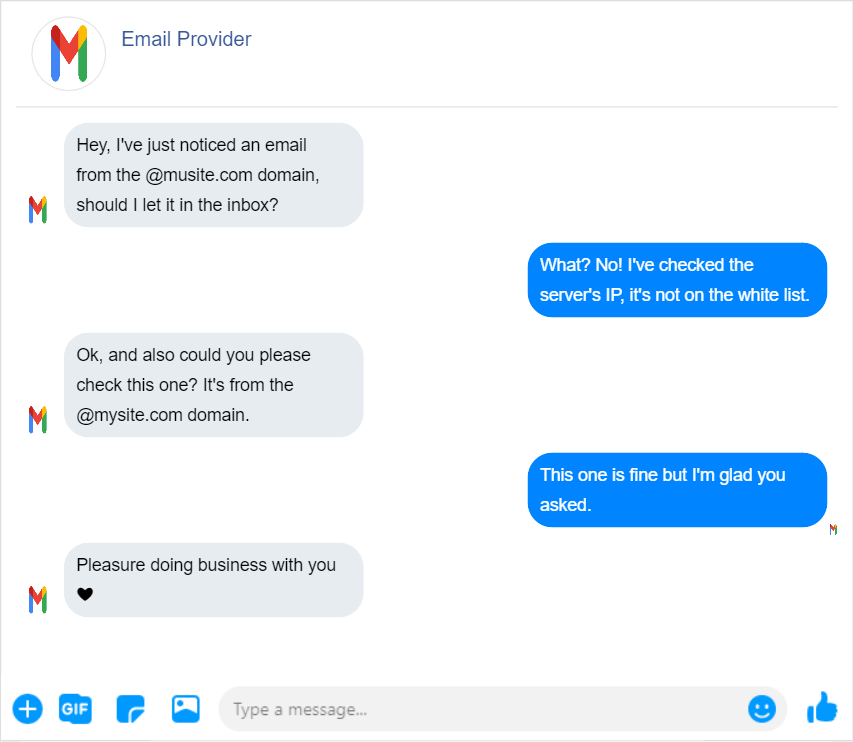
- Collect all the IP addresses you’ll send emails from.
- Make a domain white list.
- Create your SPF record and add all the necessary IP addresses.
- Publish the DNS TXT with this information.
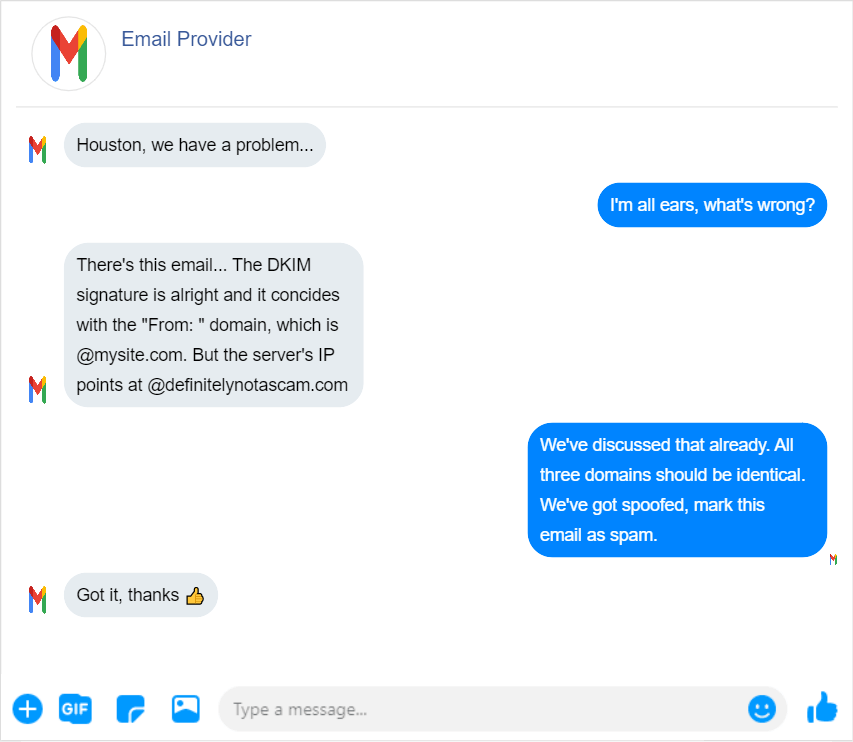
Setting up DKIM. This will require extra software. To implement DKIM, you need to install a DKIM package to your email server — for example, try OpenDKIM. You also need a DKIM key generator and a DKIM record checker — a lot of these are available online for free. Basically, you need to generate two keys, publish the private key, hide the private key, and configure the server.
If you’ve never done this before, take a look at our tutorial — we’ve covered both protocols there. But if you already have SPF and DKIM, you can set up your DMARC record. Keep in mind that both protocols must be implemented at least 48 hours before setting up the DMARC record.
Define your policy record
As we’ve mentioned earlier, a DMARC record looks like a bunch of variables with values — some of them are mandatory, others are not. Take a look at this spreadsheet to learn more:
| Variable |
Is it mandatory? |
Meaning |
Possible values |
| v |
Yes |
The version of your DMARC record |
DMARC1 |
| p |
Yes |
What to do with emails that failed authentication |
- none — do nothing and send the email to the intended recipient
- quarantine — send the email to the recipient’s spam folder and let them see if it was a mistake
- reject — abort sending, this is the strictest option
|
| rua |
Not mandatory but wouldn’t hurt |
The email for DMARC reports |
mailto:[email protected]
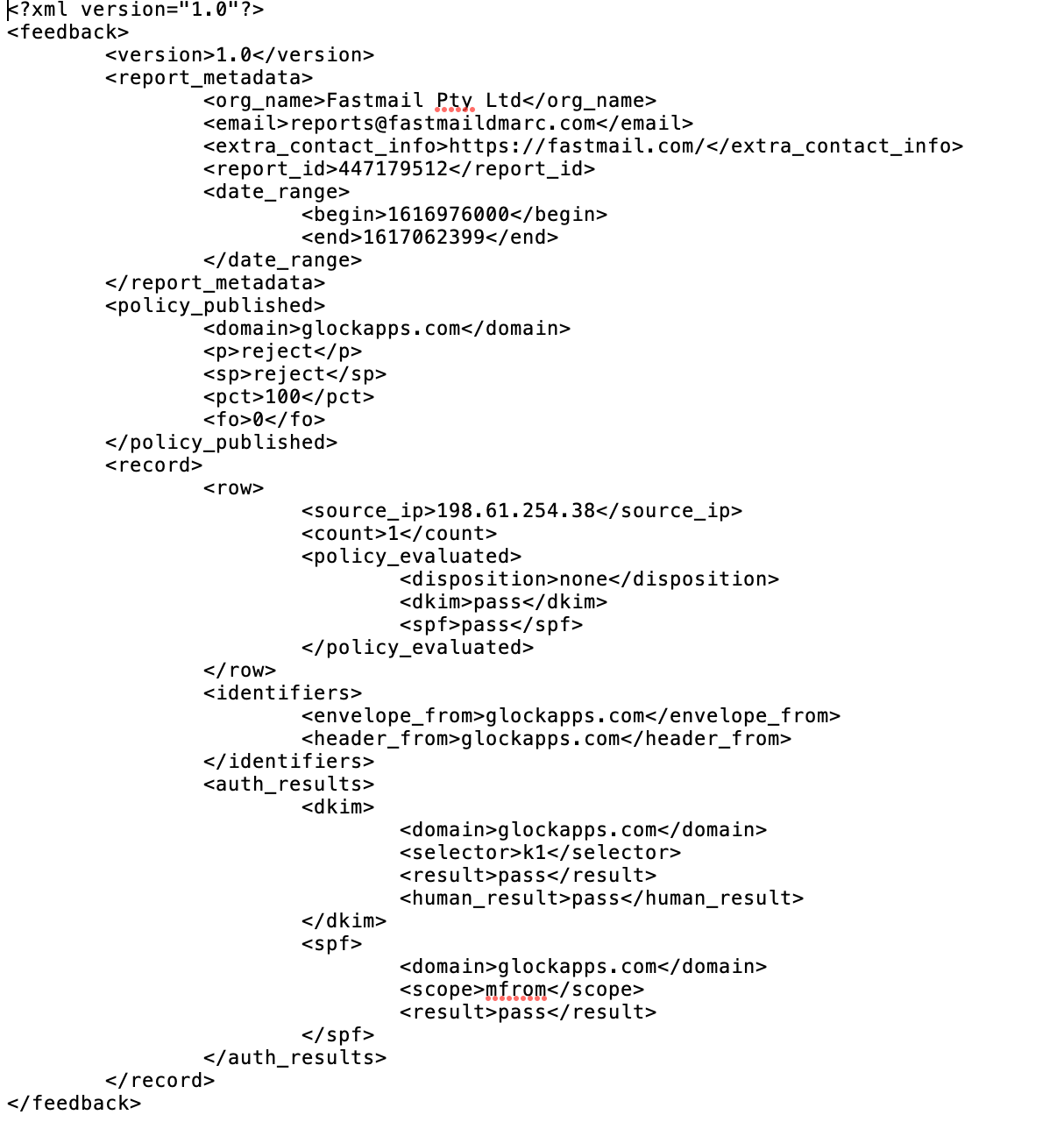
If you add this tag to your record, your email provider will aggregate daily XML reports and send them to the email address of your choice. |
| pct |
No |
Sets the percentage of invalid emails that fall under the DMARC policy |
1 to 100 |
| sp |
No |
Sets a different policy for subdomains |
The same as for p — none, quarantine or reject |
| adkim |
No |
Sets the strictness level of DKIM matches |
- s — only 100% DKIM matches with the main domain name, other cases will fall under the DMARC police
- r — allows partial matches, any valid subdomain is accepted, the default setting
|
| aspf |
No |
Sets the strictness level of SPF checks |
- s — only the main domain is accepted
- r — allows partial matches like subdomains, the default setting
|
Let’s decode this example of a DMARC policy record.
It means that 45% of emails that failed authentication will be sent to spam folders — and reports about these cases will be sent to [email protected]. Using the pct tag is useful if you’re only starting to implement DMARC — you can slowly increase the percentage to reach 100%.
Let’s take a look at another example.
It means that none of the emails that failed authentication will be delivered — and reports will be sent to [email protected].
The rejection policy seems the safest option but it leads to a lot of false positives. For example, if you didn’t double-check your white list of email domains, emails from the SaaS payment system you use might fail to reach recipients. That’s why we suggest using this policy only if you know that someone is already sending spoofed emails pretending to be your company. We suggest using the quarantine policy — in this case, it’s up to recipients to decide whether your email is trustworthy. And, since you receive reports, you can use this information to improve both your mass mailing process and email content.
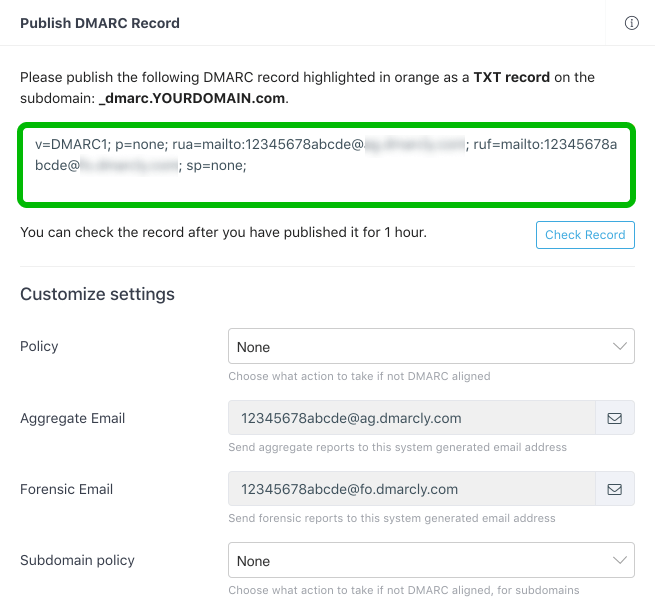
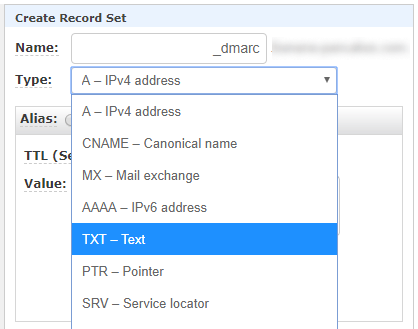
Publish a DMARC record
As we mentioned earlier, DMARC is a DNS TXT record. To publish such records, visit your hosting provider and choose “Create record”. Then, choose the TEXT type in this drop-down list.