What a DKIM record is and how it works
The scope of influence of DKIM conventionally is divided into two parts: what happens on the sending server and what happens on the receiving server. For the DKIM authentication method to work, two keys are created: a private key and a public key.
The private key encrypts the data of the sender in the headers of each email sent. The headers are not visible to the recipients of emails. The private key for each domain is stored on the server.
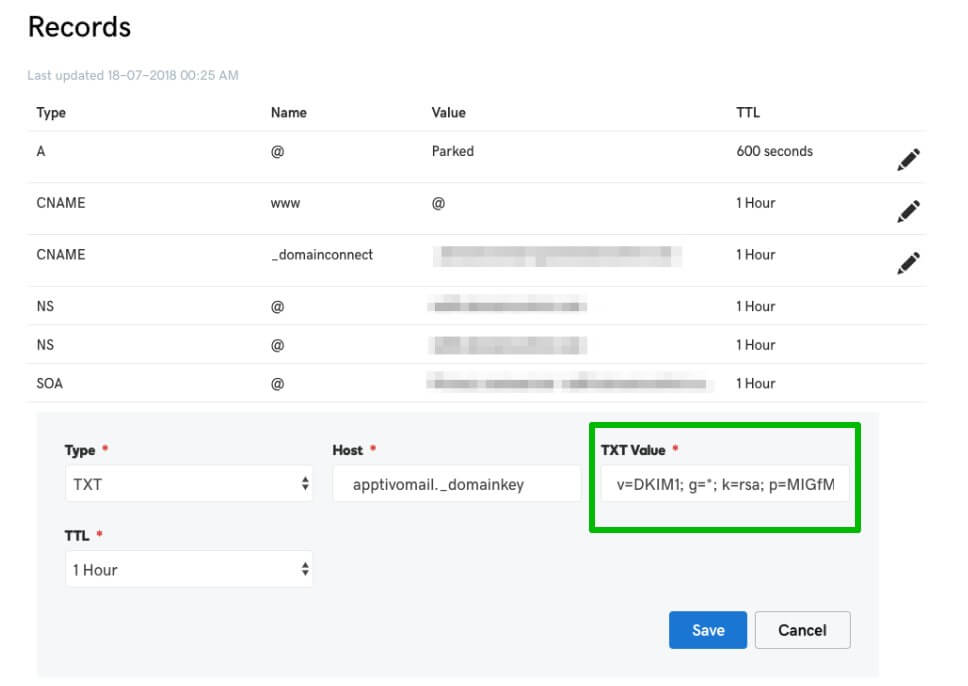
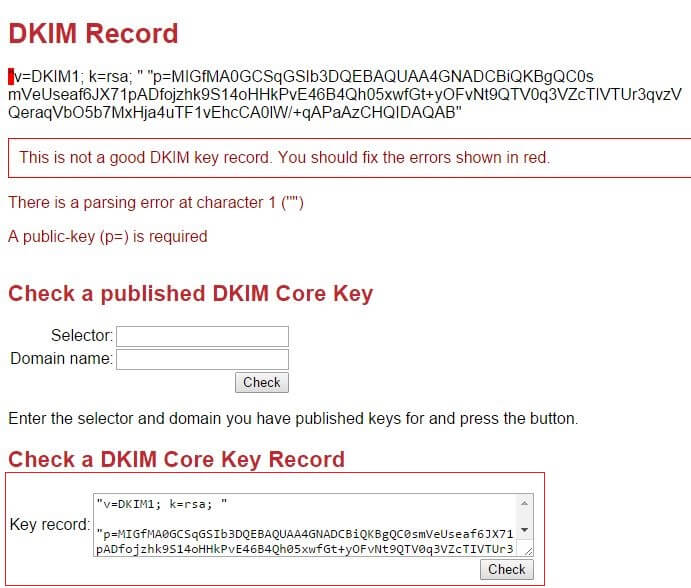
A public key is a DKIM signature or DKIM record. It looks like a txt record that is added to the DNS zone settings of a domain. It looks like this:
| v=DKIM1; k=rsa; t=s; p=””*******….”” |
Where:
| Variable |
Meaning |
| v |
The DKIM version. |
| k |
The key type, always specified as “rsa”. |
| p |
The key, which is created through the settings of email services, or it can be generated on a third-party platform. |
Sending a signed DKIM message
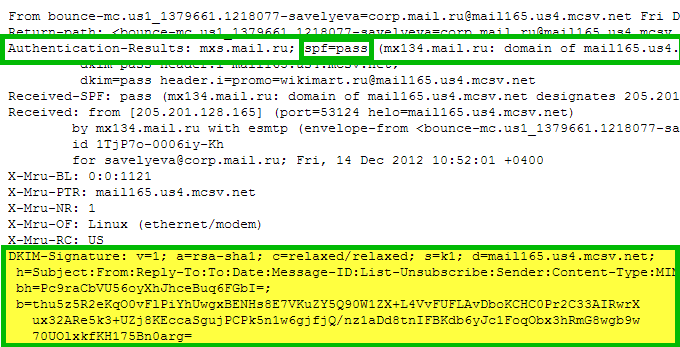
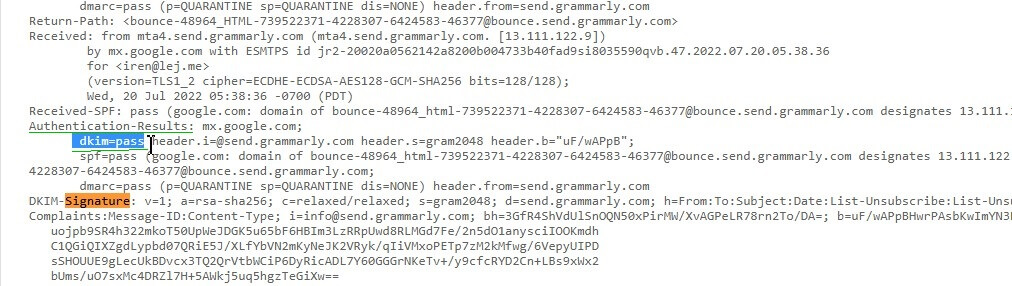
A key pair is generated for you when you use a DKIM-enabled email service provider. This private/public key combination is what constitutes the key pair. The sender’s email service provider uses the private key to encrypt the message before delivery. The DKIM signature, which contains the sender’s DKIM identity, appears in the DKIM-Signature header. Everything required for verification from the recipient server is included in this signature.
Verifying a signed DKIM message
The message recipient’s email service extracts the DKIM signature from the header of the email and retrieves the corresponding DKIM record from the DNS server of this domain after it has received it. The security and legitimacy of the message are verified using the supplied public key.
If the message was not altered, the check was passed, changed – failed, and the email is sent to SPAM.