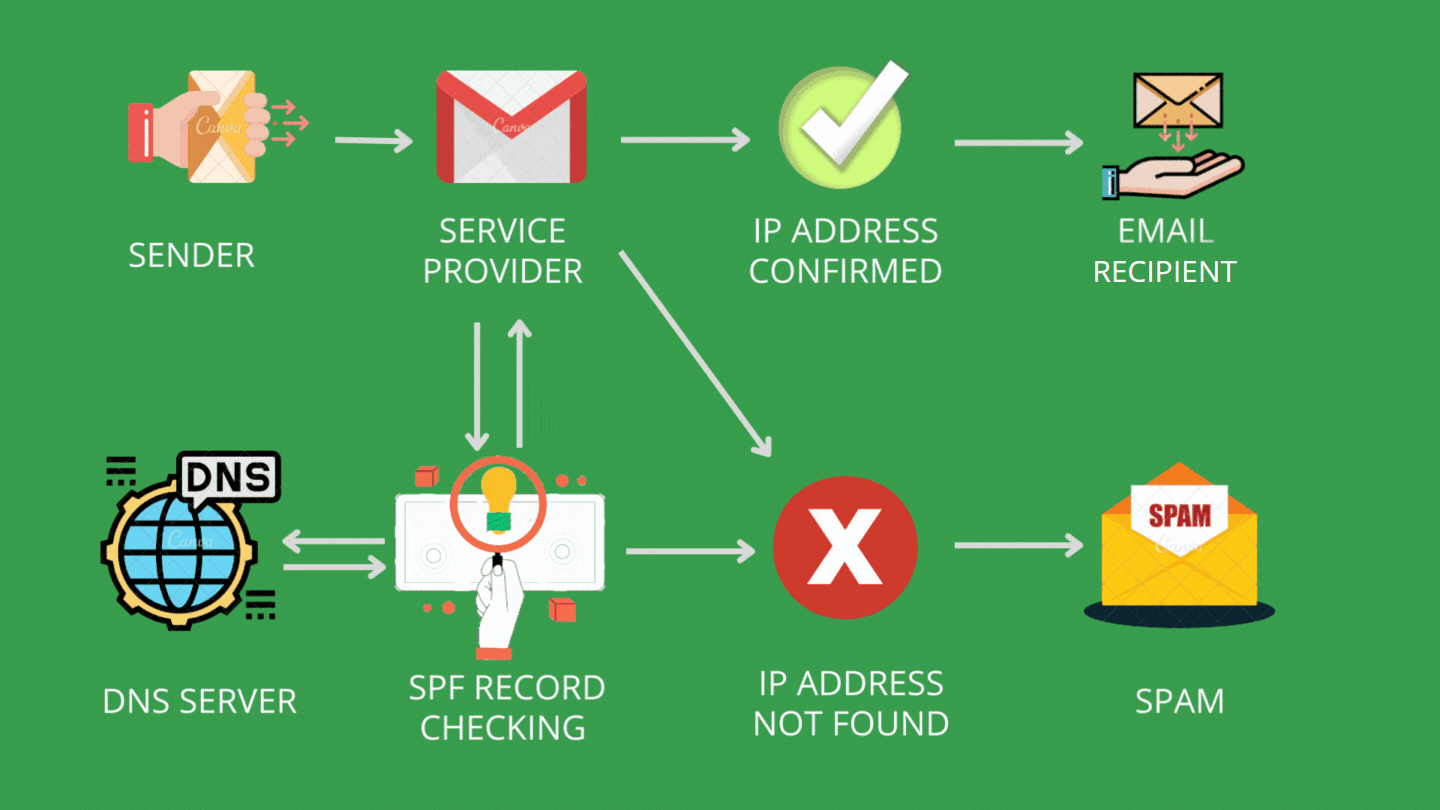
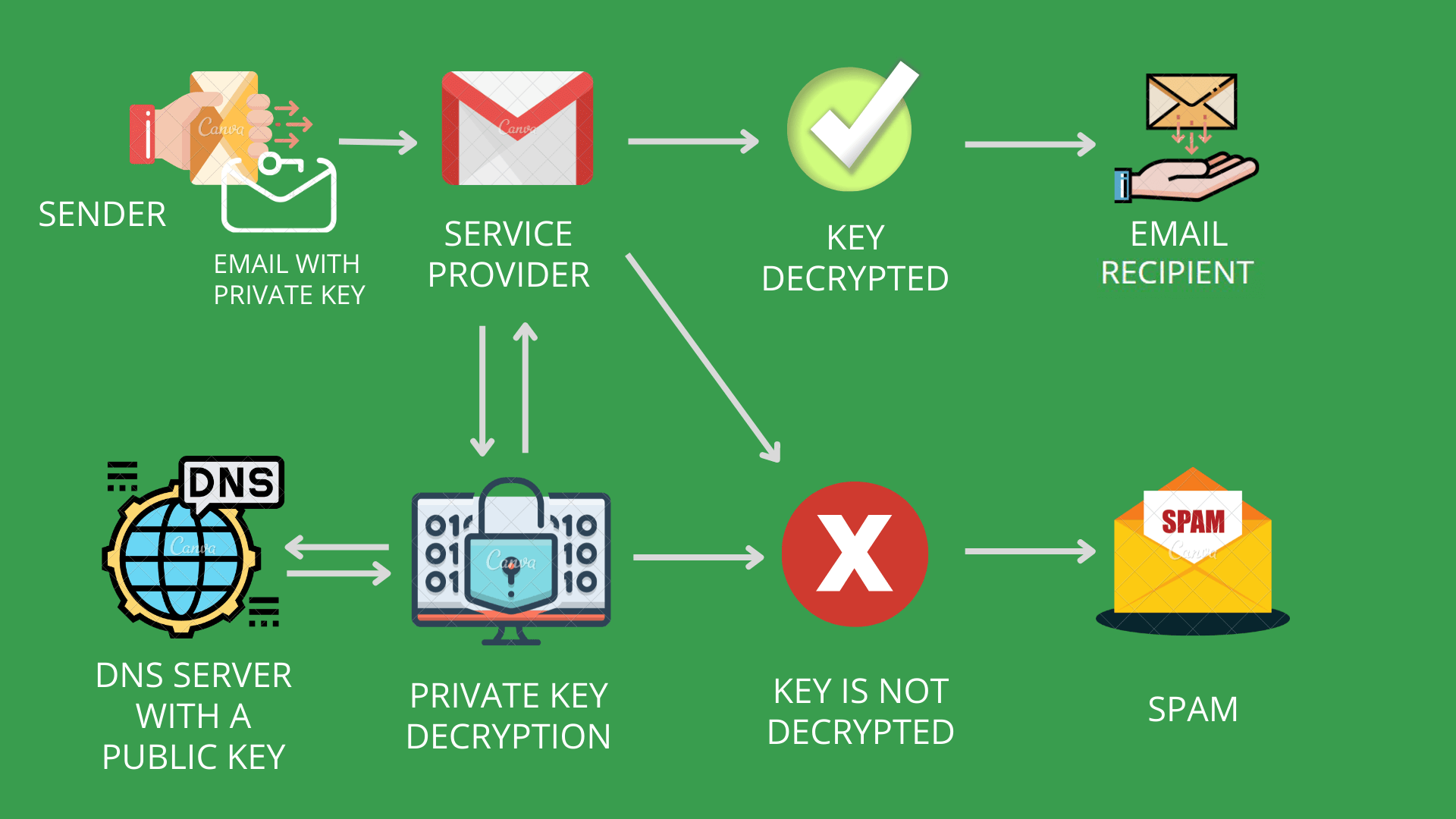
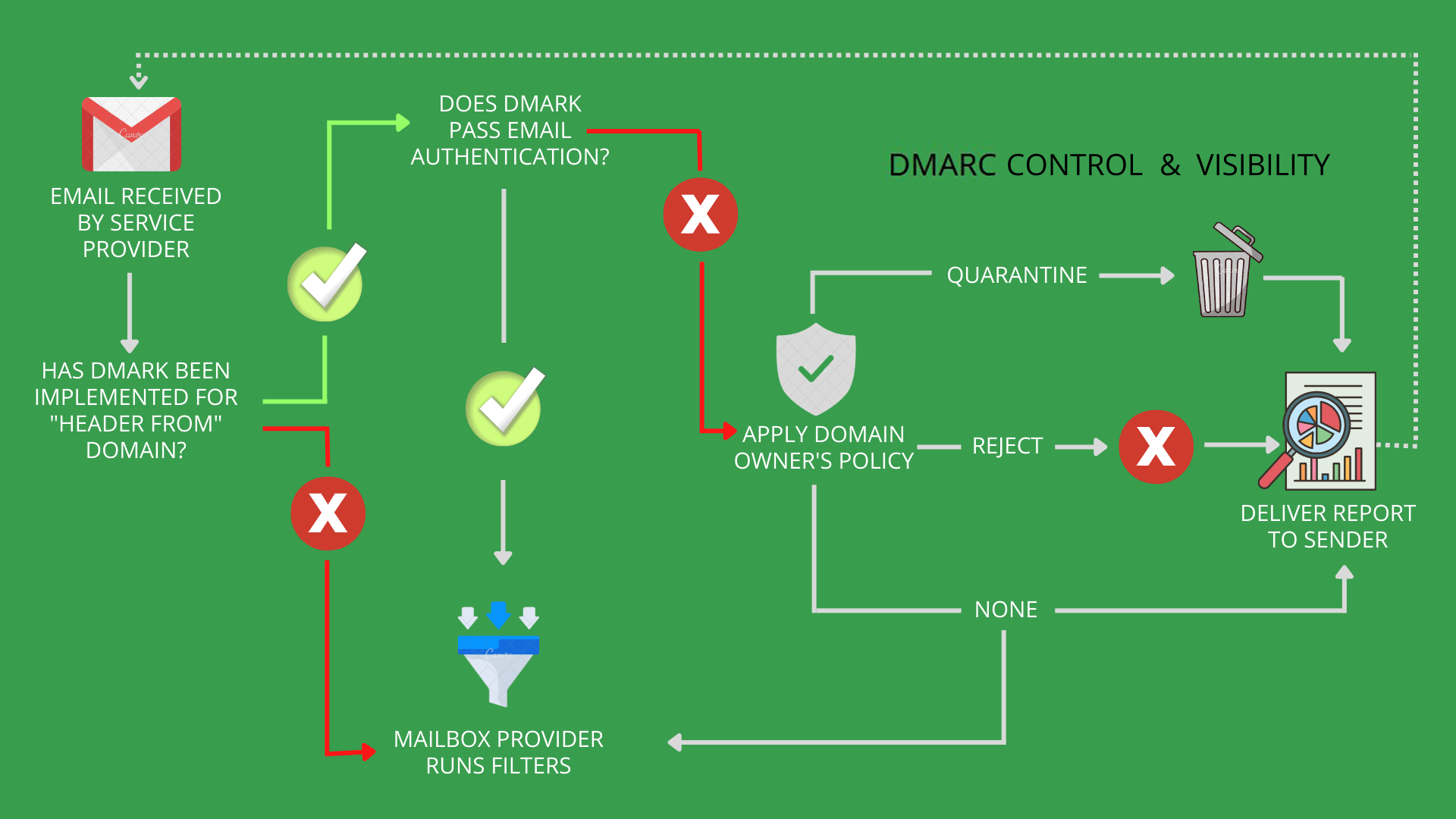
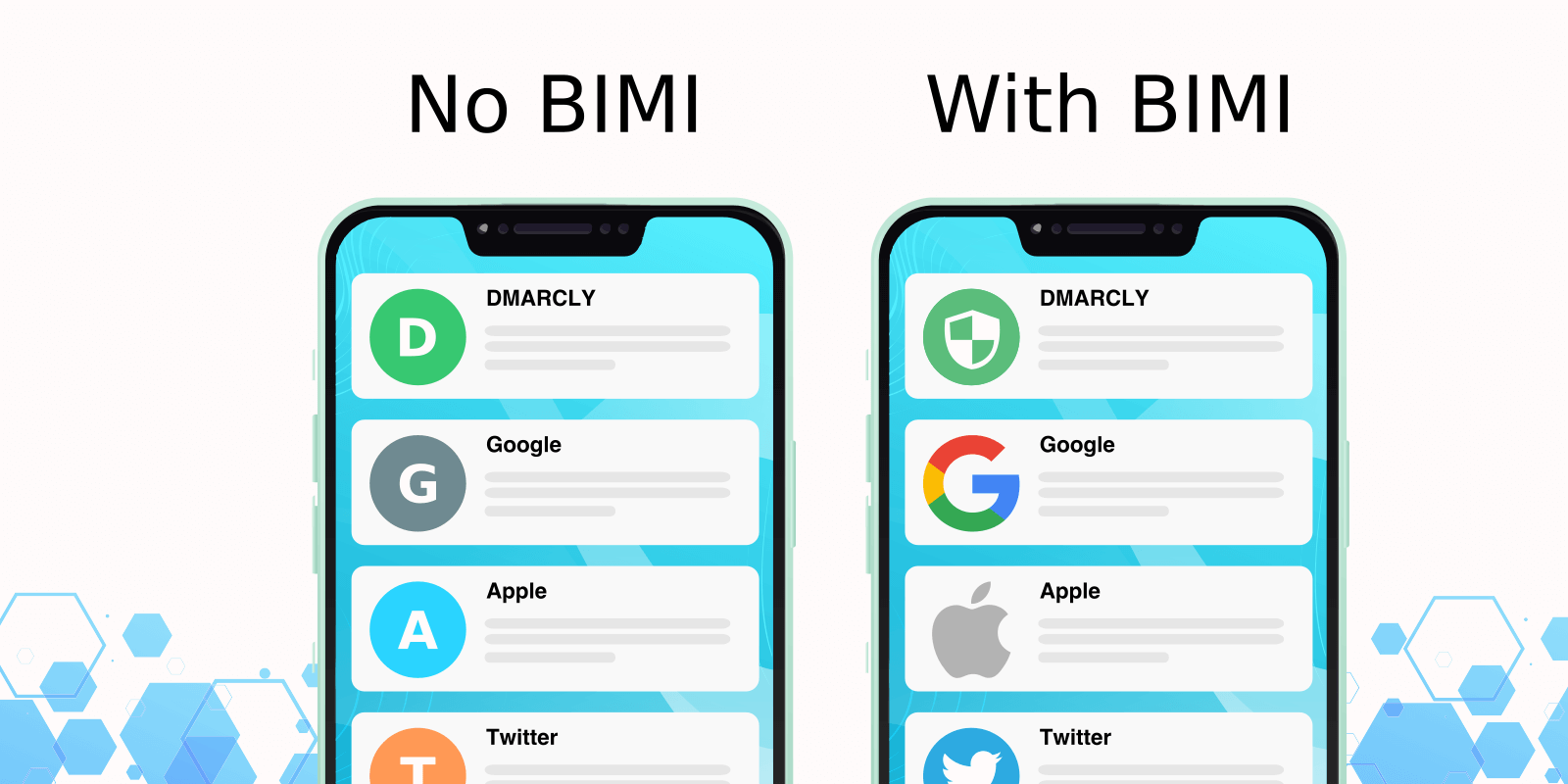
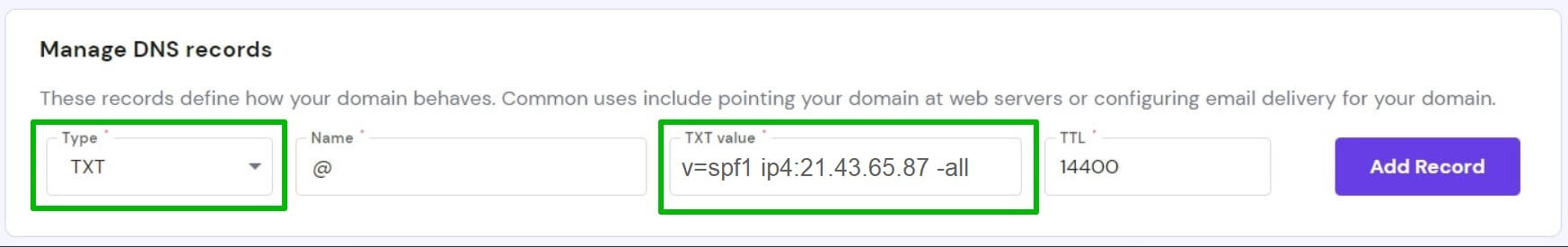
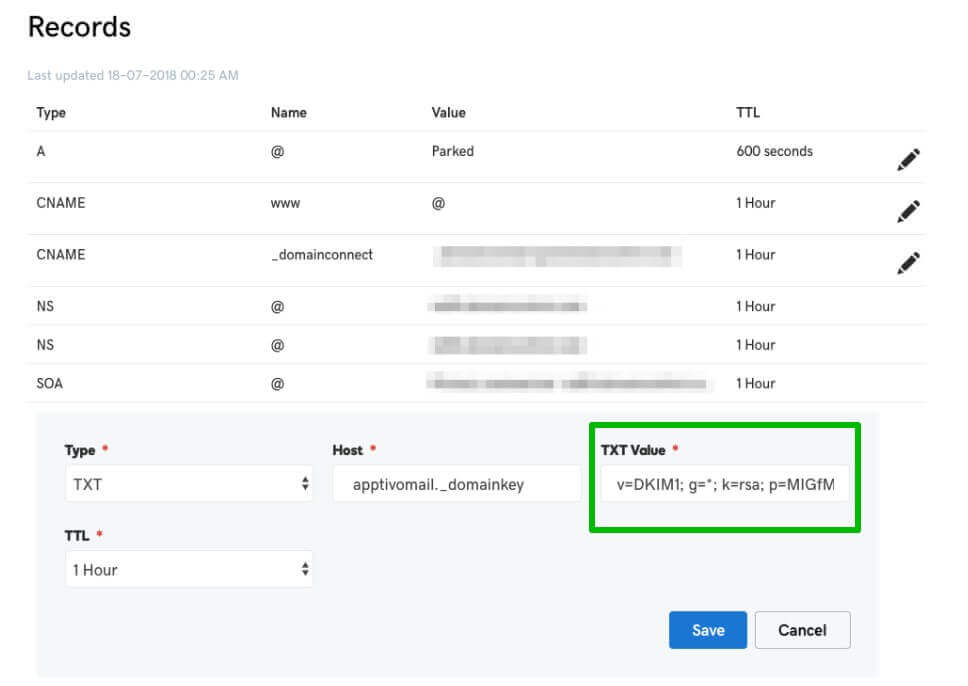
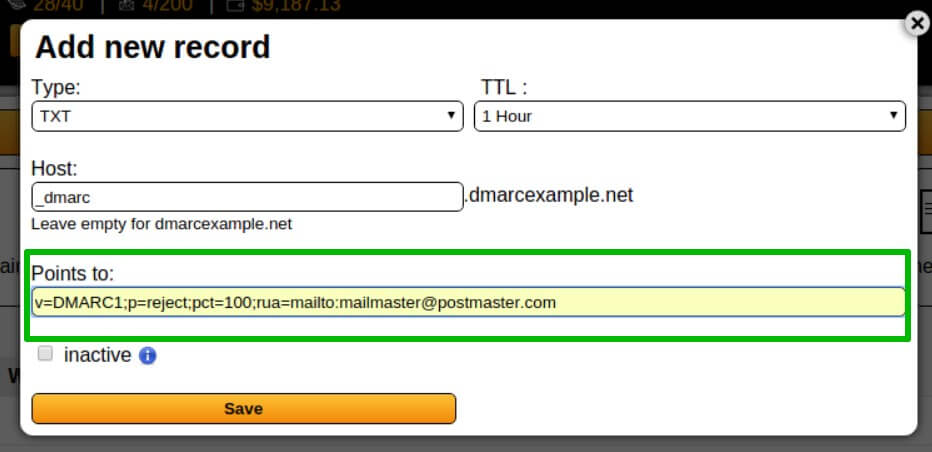
Setting up email authentication is important for making sure your email marketing campaigns are effective as it helps to provide security and improve the deliverability of your emails. It involves several measures that we describe in this guide. Read on to make sure all your emails are properly authenticated and able to reach their recipients.