Worried your email will end up in spam? Not with Selzy! With a 99.8% delivery rate, your emails land in the right inboxes — and your product in your customers’ hearts. Just ask our 50,000+ happy clients.
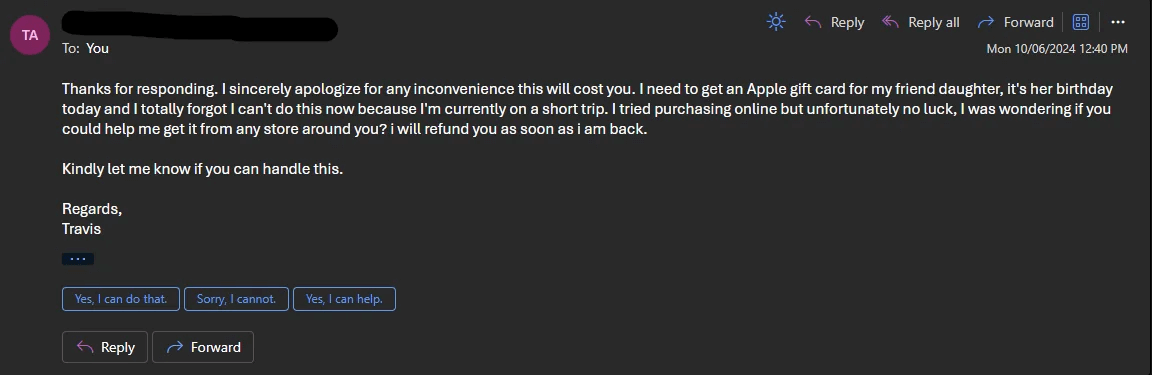
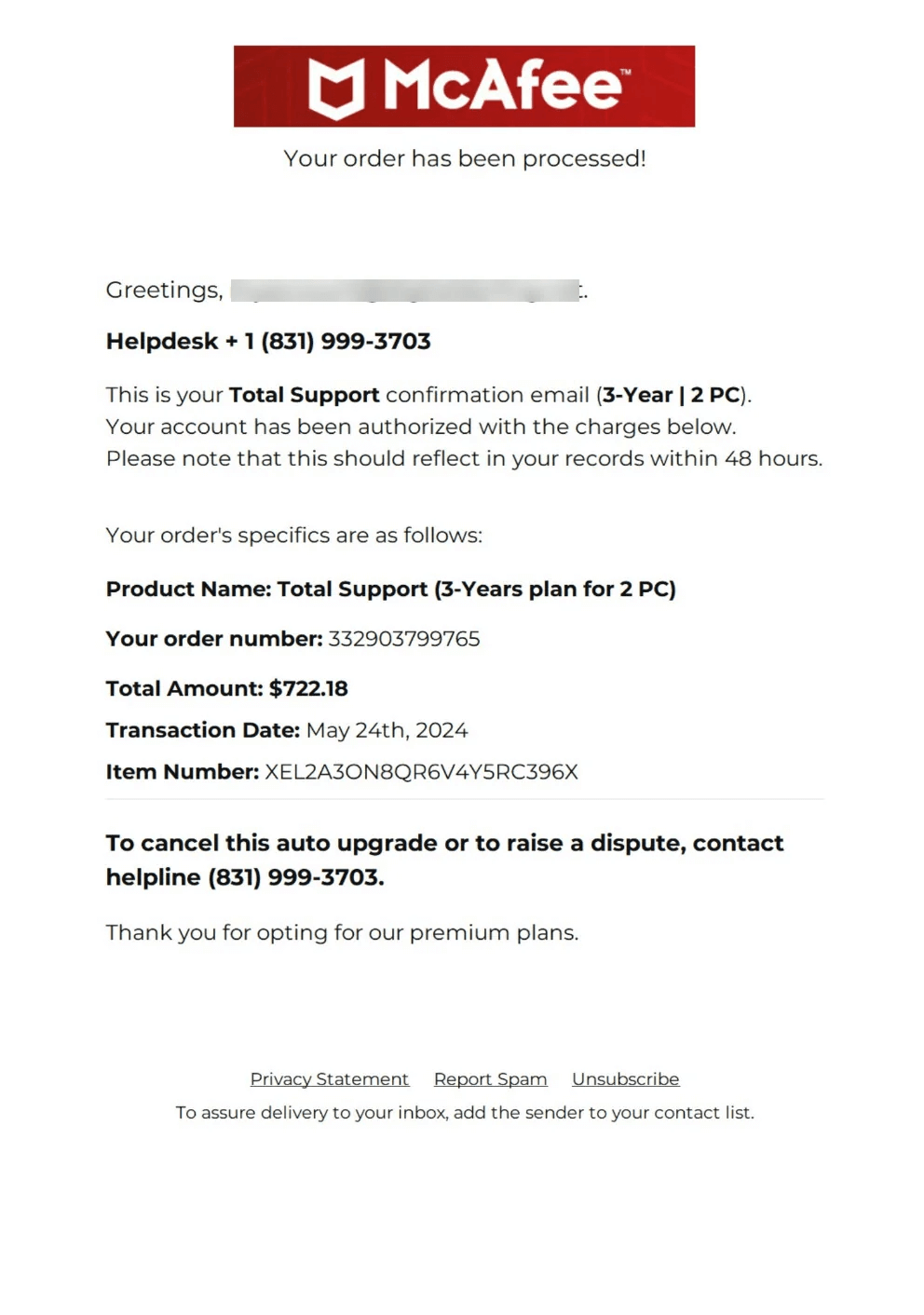
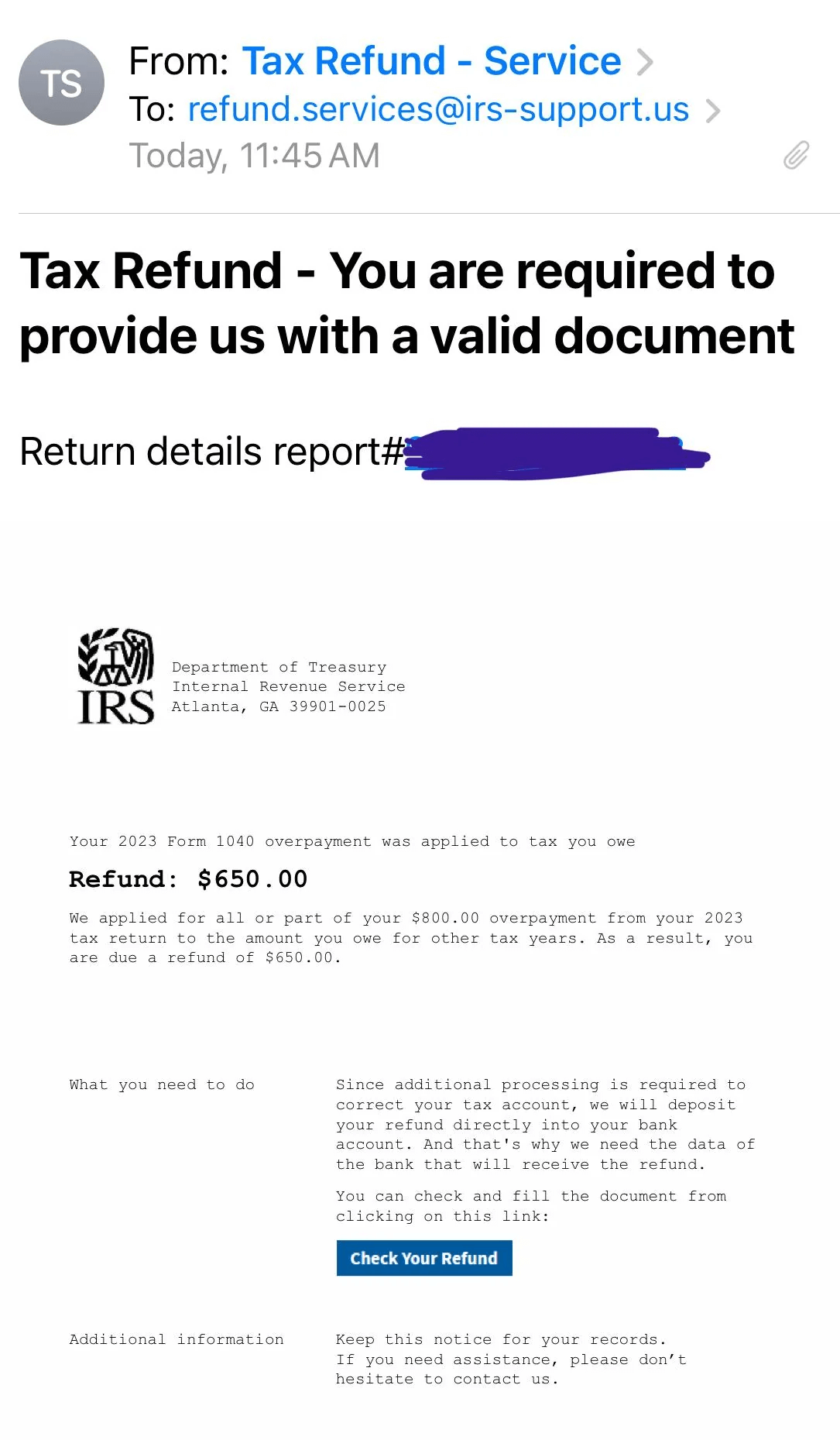
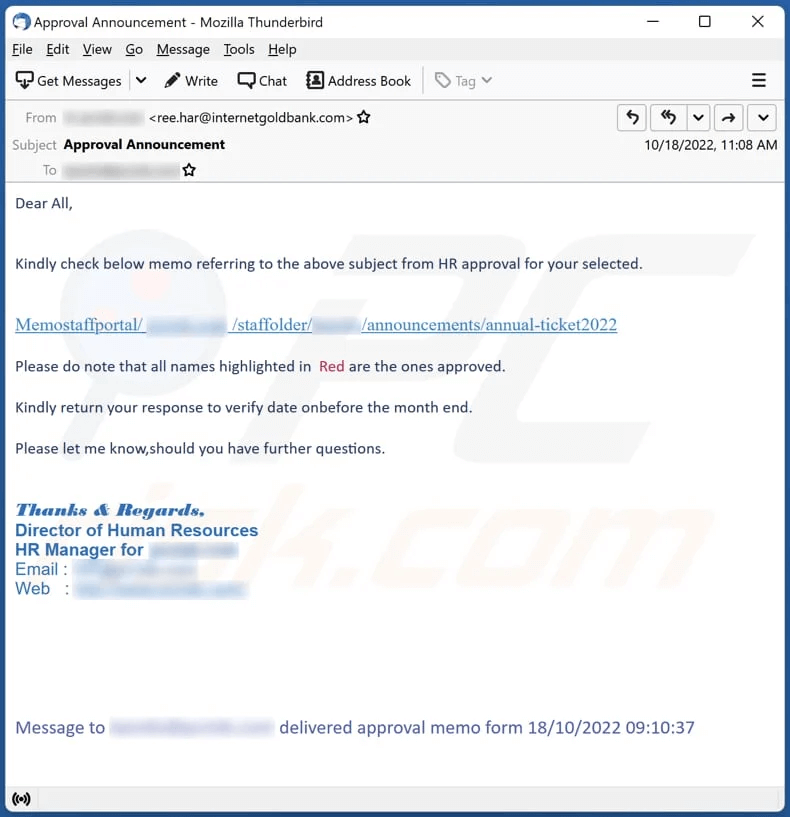
Why am I getting spam emails?
Let’s take a look at some common methods that spammers use to obtain email addresses — and how to protect yourself from junk mail.
Data breaches
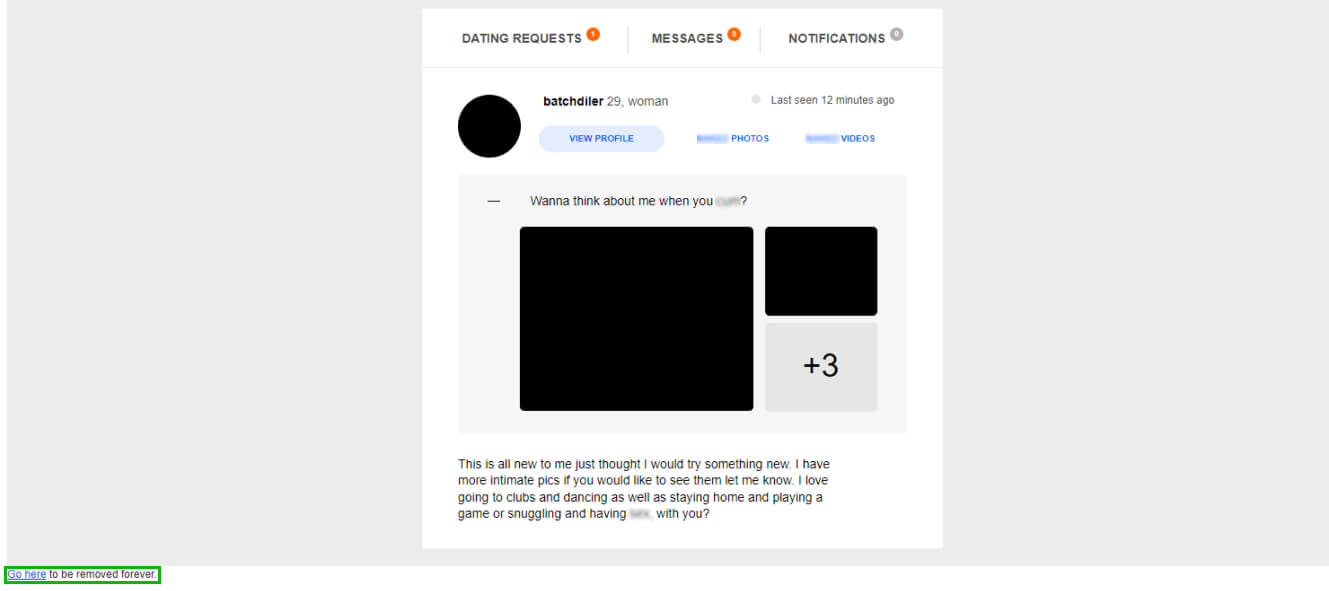
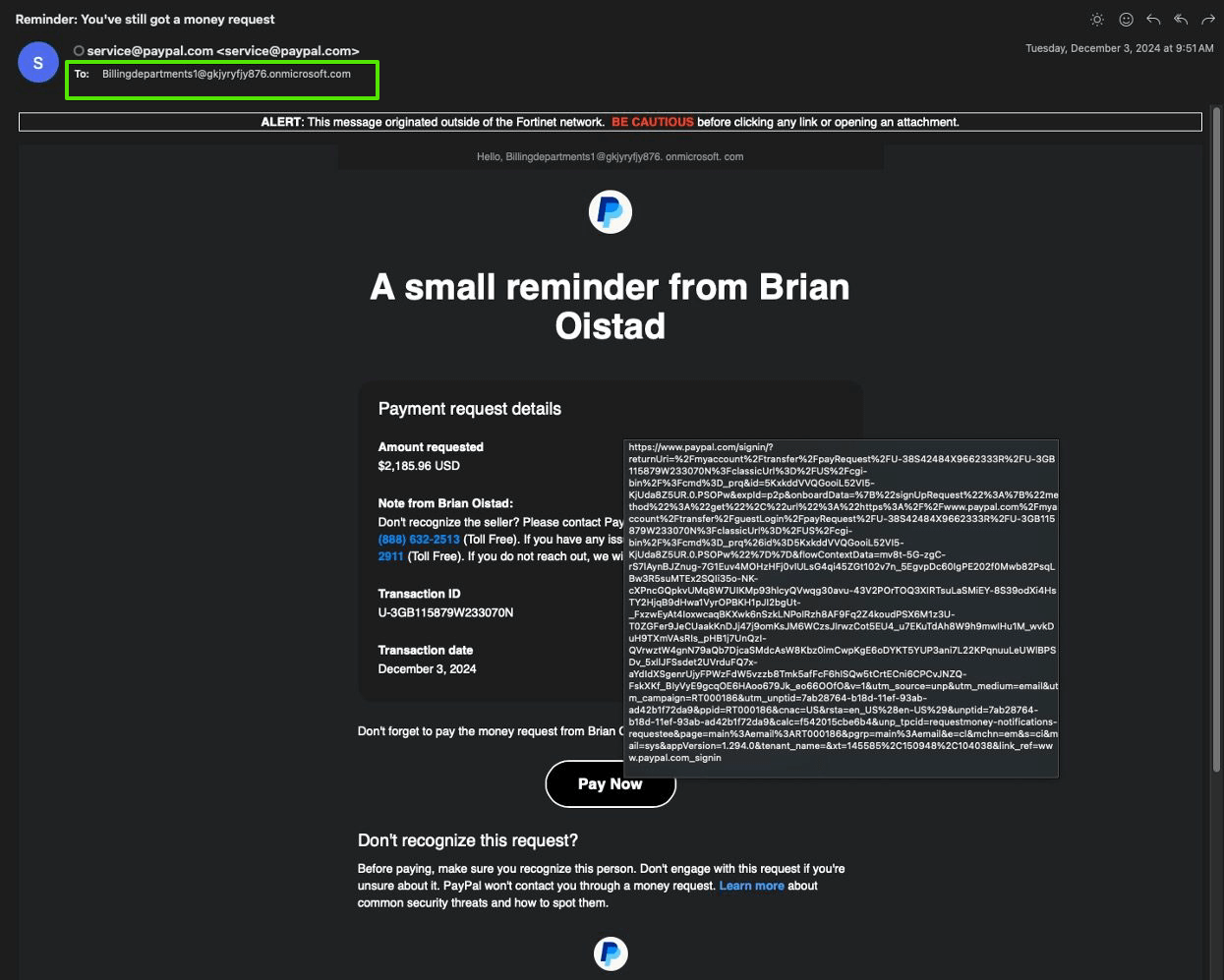
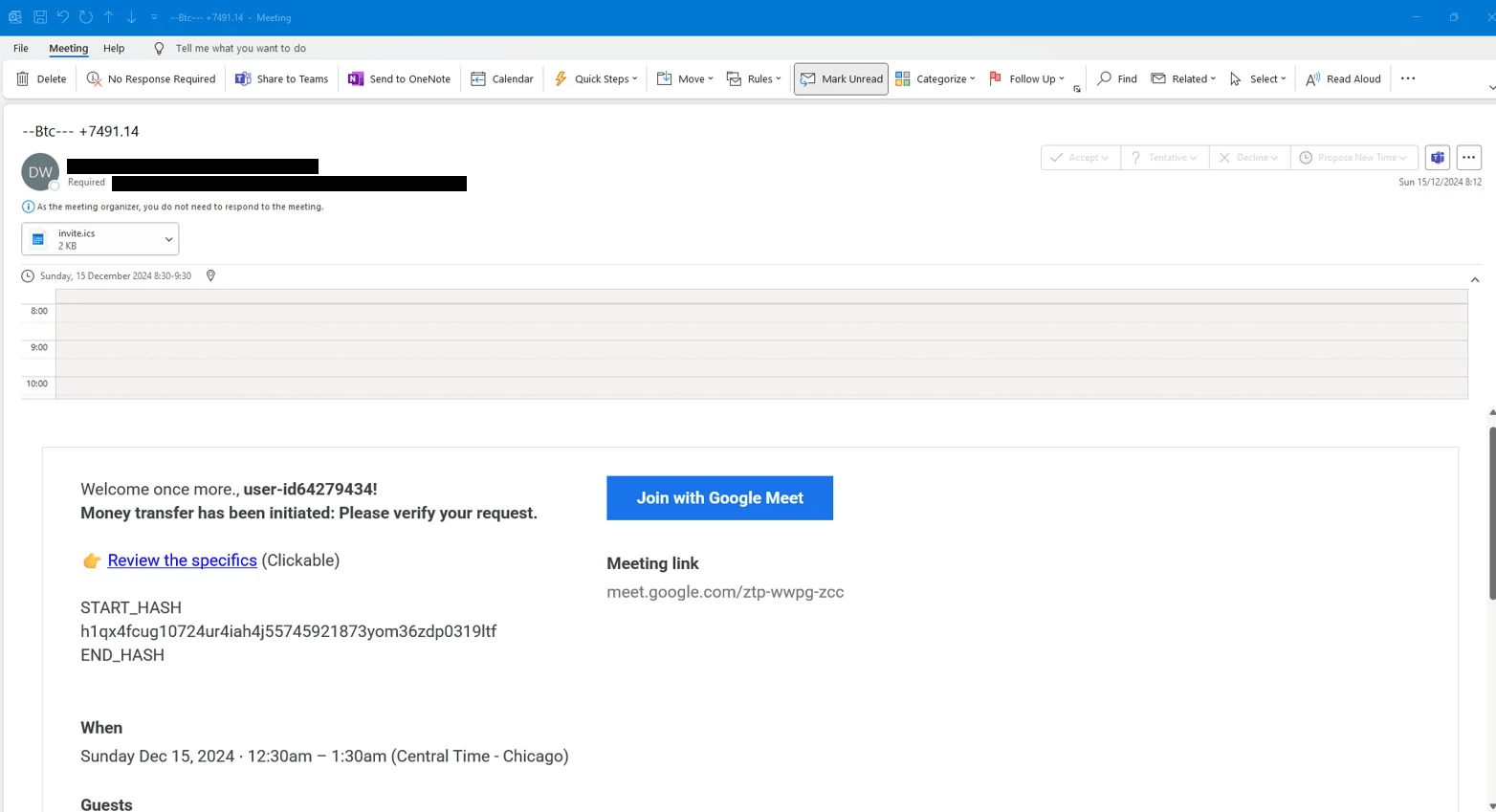
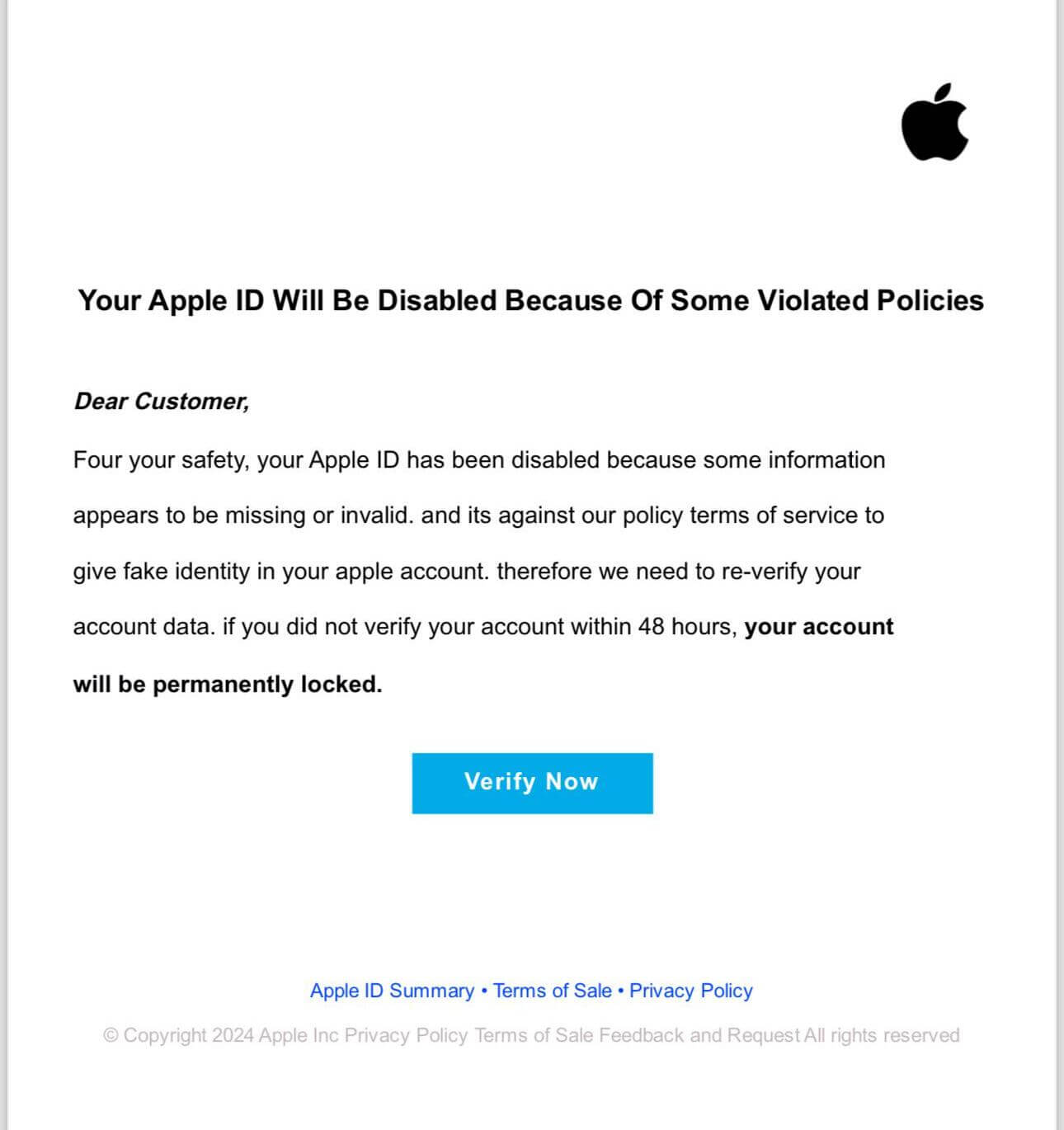
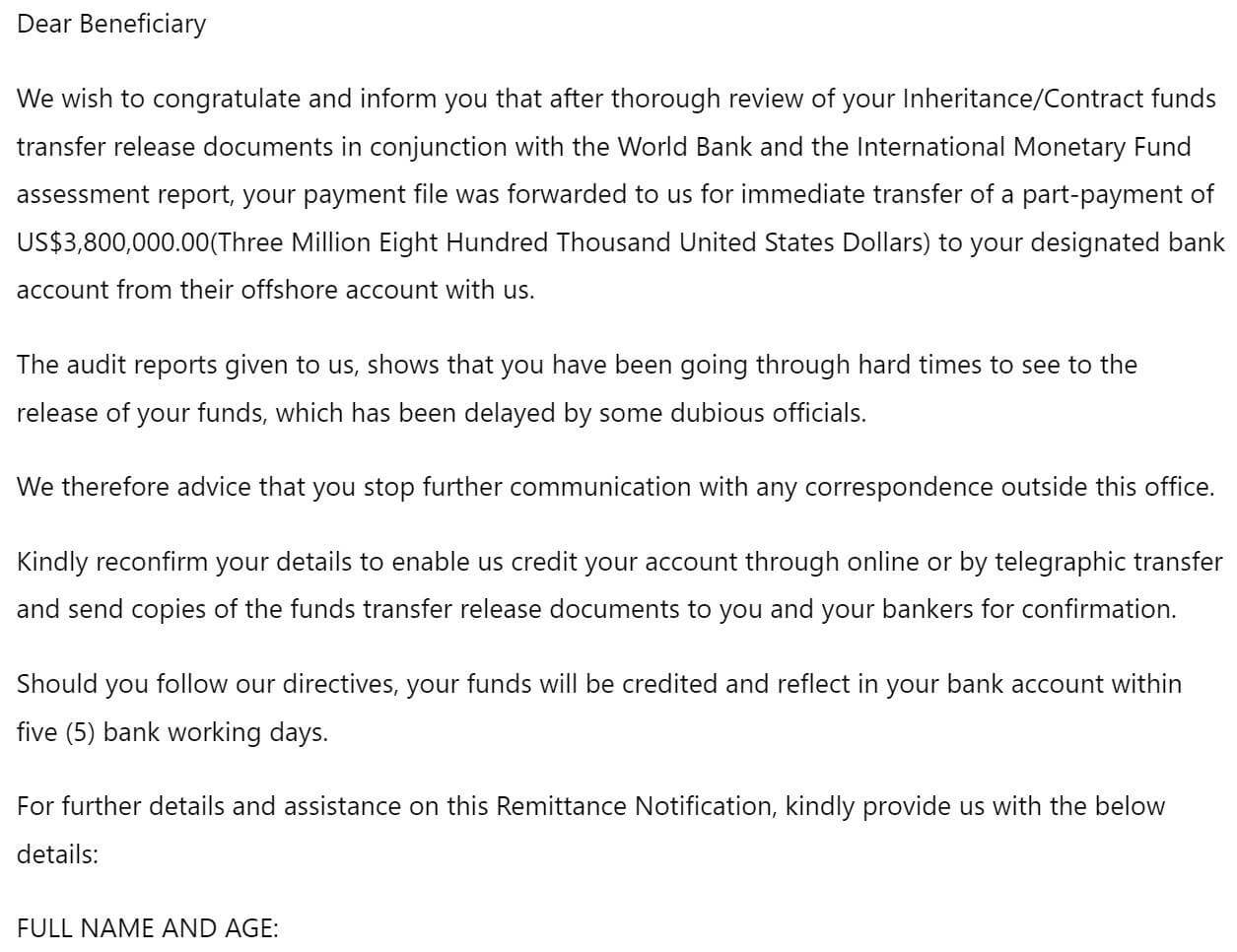
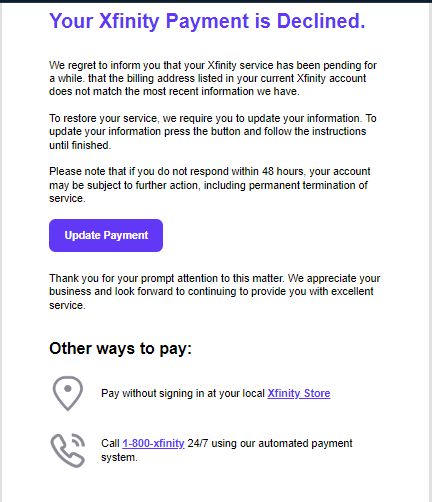
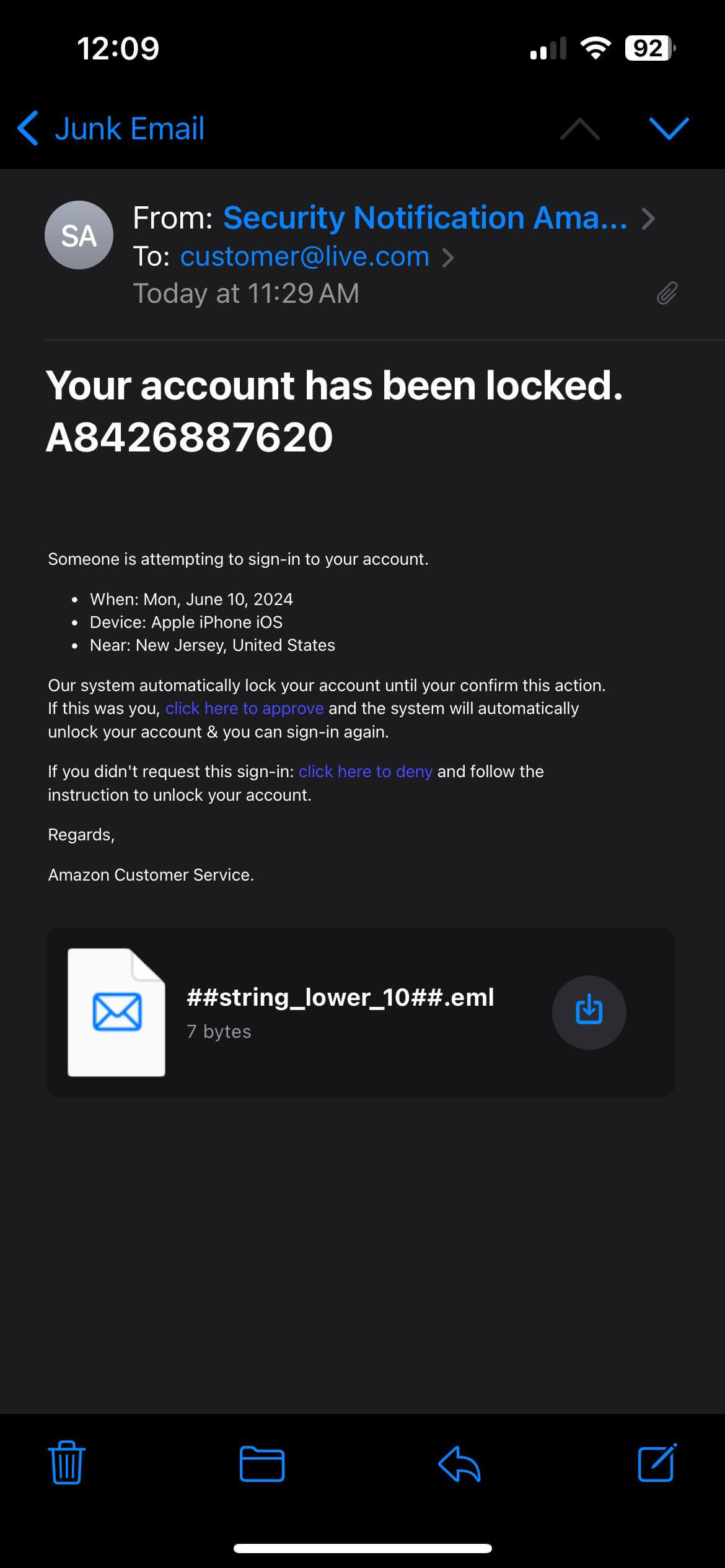
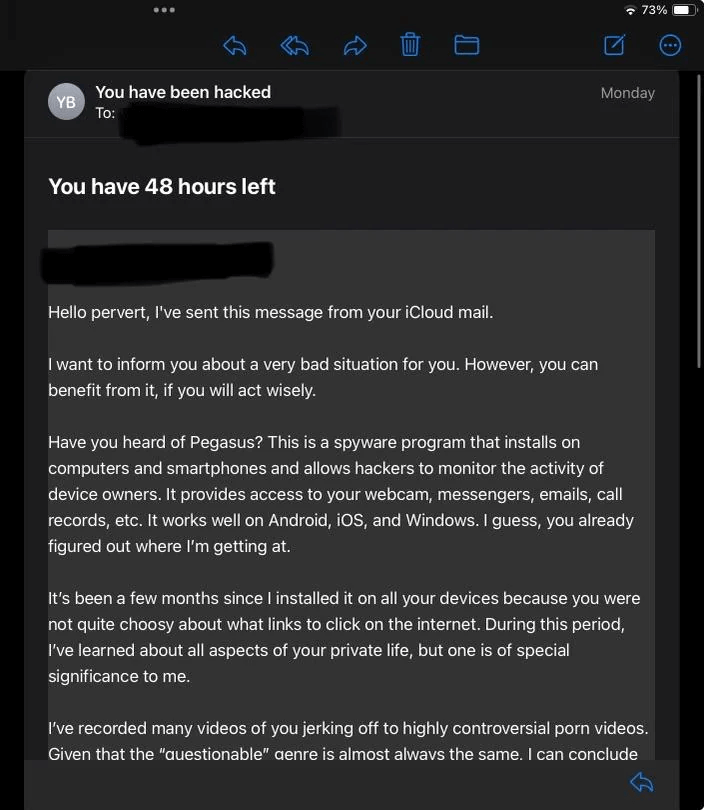
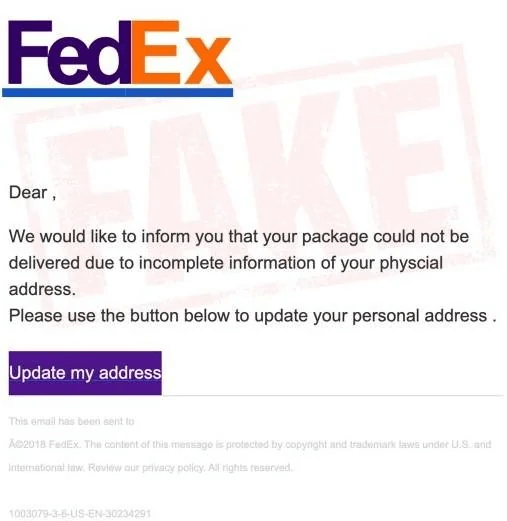
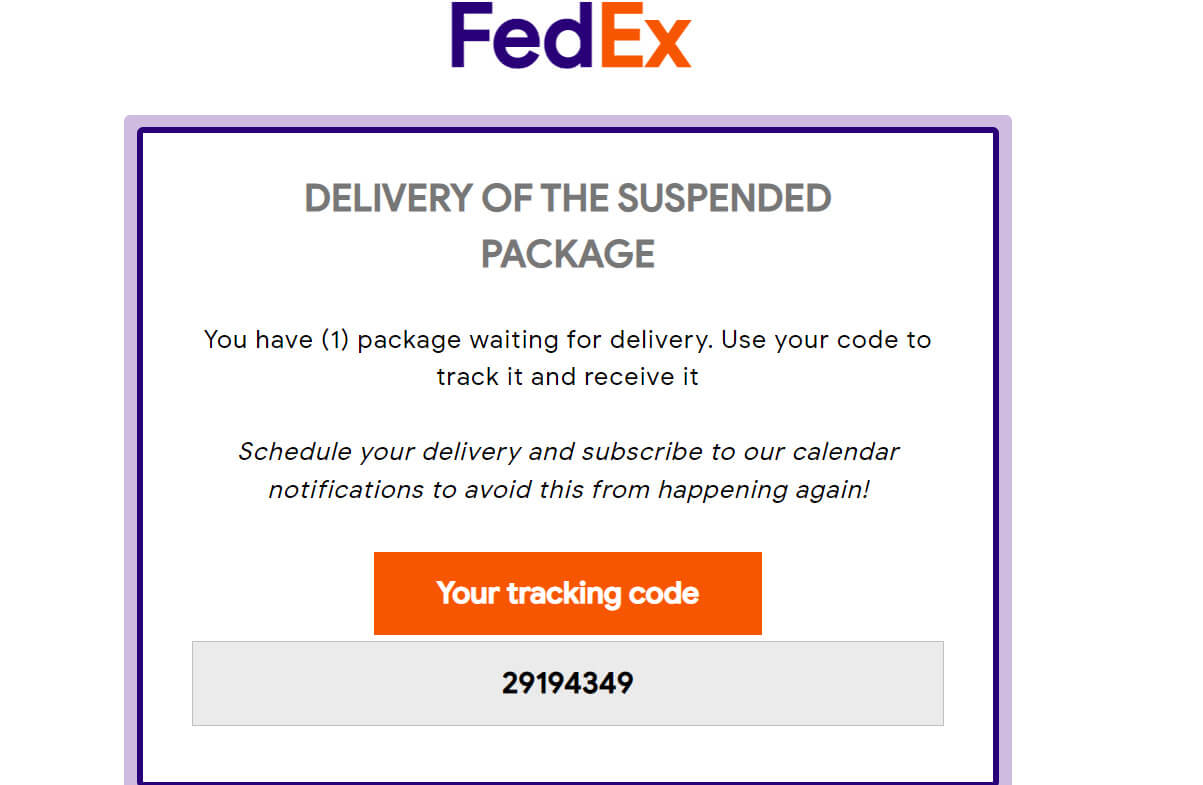
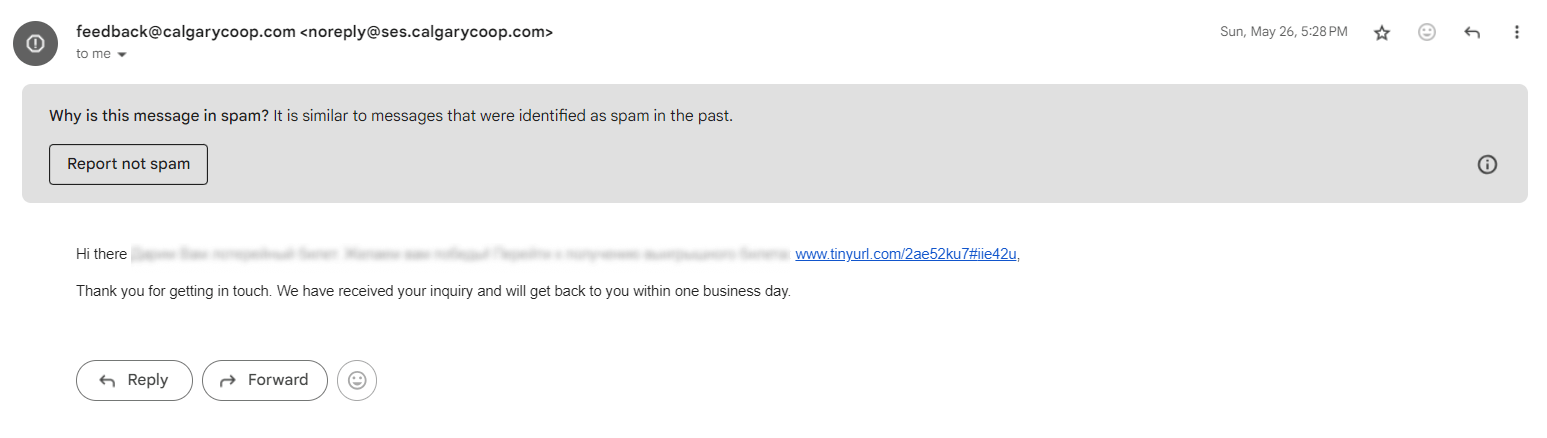
Many web services and mobile apps require an email address for signing up. When you create an account, your email goes into a list. Companies know how to send mass emails — they use this list for notifications and marketing materials. Then, data breaches happen, and the entire contact lists with other personal data end up on sale. Finally, spammers use these lists to send malicious emails.
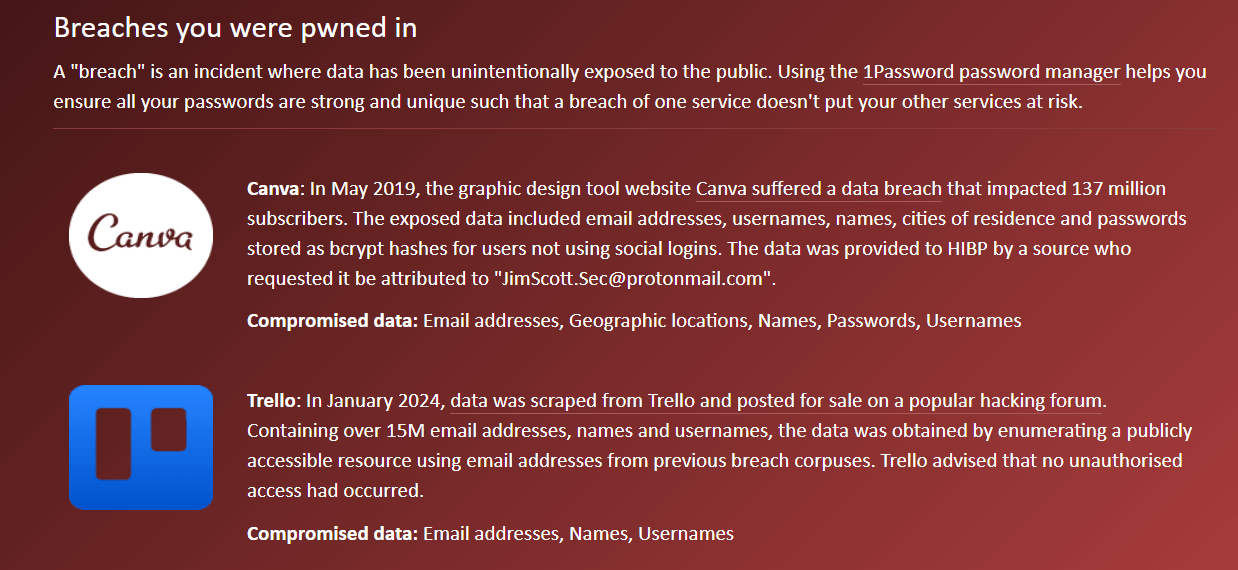
Even large corporations suffer from security breaches — in fact, this happens almost every other week. In 2024, there were 3,158 data compromises, according to the Identity Theft Resource Center. That resulted in the issue of more than a billion data breach notices.
No one can prevent such breaches, and the only way to protect yourself from them is to either avoid any online services in general or use a temporary email service — and that’s not always possible. However, if you suddenly started receiving spam emails, checking if your data was compromised is the right move. There are a number of apps to help you, with Have I Been Pwned? being one of the most popular options. Enter your email address, and the service will check its database for any matches. If your address was found in a breach, you’ll receive a message with a list of incidents.